Our reports
The Microsoft mission is to empower every person and every organization on the planet to achieve more, and all of our technologies are designed to further that mission. We protect the privacy of our customers and work to earn their trust every day. At the same time, Microsoft recognizes that law enforcement plays a critically important role in keeping our customers—and our technology—safe and free from abuse or exploitation. We are hopeful that this report can both inform the public and contribute to the discussion about how best to strike the balance between the privacy of our customers and the legitimate needs of governments to protect and serve their citizens.
Our principles
While these reports include separate sections for requests based on law enforcement, national security, and civil authorities, Microsoft follows the same principles for responding to all government requests for customer data.
- Microsoft reviews every legal demand to ensure it is valid and complies with applicable laws. A subpoena or its local equivalent is required to request non-content data, and a warrant or its local equivalent is required for content data.
- Microsoft discloses customer data only when legally compelled to do so.
- Microsoft does not provide any government with direct or unfettered access to customer data.
- Microsoft does not provide any government with our encryption keys or the ability to break our encryption.

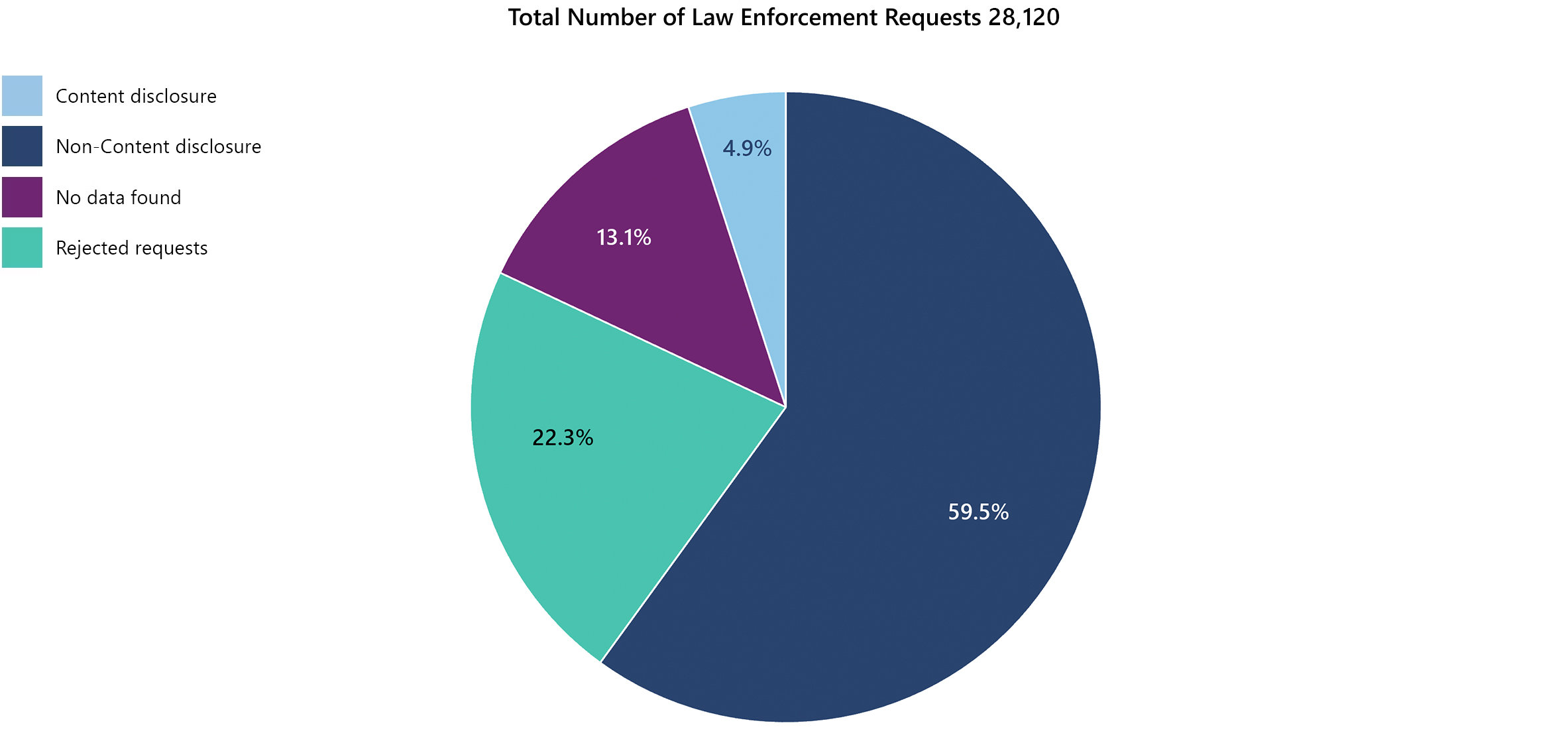
Data requests received for all Microsoft Services from July to December 2024
Requests for Consumer Data
A consumer service is generally one subscribed to and used by an individual in their personal capacity.
Some examples include Hotmail/Outlook.com, OneDrive, Xbox Live, and Skype.
FAQ regarding consumer requests
-
Yes. Microsoft gives prior notice to users whose data is sought by a law enforcement agency or other governmental entity, except where prohibited by law. We may withhold notice in exceptional circumstances, such as emergencies where notice could result in danger to an identifiable person or group (e.g., child exploitation investigations), or where notice would be counterproductive (e.g., where the user’s account has been hacked). Microsoft also provides delayed notice to users upon expiration of a valid and applicable nondisclosure order unless an exceptional circumstance remains present.
-
Occasionally. The CLOUD Act amended U.S. law to make clear that law enforcement may compel service providers with minimum contacts with the U.S. to disclose data that is in their “possession, custody, or control” regardless of where the data is located. This law, however, does not change any of the legal and privacy protections that previously applied to law enforcement requests for data – and those protections continue to apply.
In the first half of 2024, Microsoft received 5,560 legal demands for consumer data from law enforcement in the United States. Of those, 52 warrants sought content data which was stored outside of the United States.
For additional information about how Microsoft responds to law enforcement requests for data, see the “General FAQ” section below.
Requests for Enterprise Customer Data
For purposes of this report, an “enterprise customer” generally includes those organizations or entities (commercial, government, or educational) that purchase more than 50 “seats” for one of our commercial cloud offerings, such as Microsoft 365 or Dynamics 365, or purchase an Azure subscription. Those organizations, in turn, may provide services, such as email, to individual employees, students, or others.
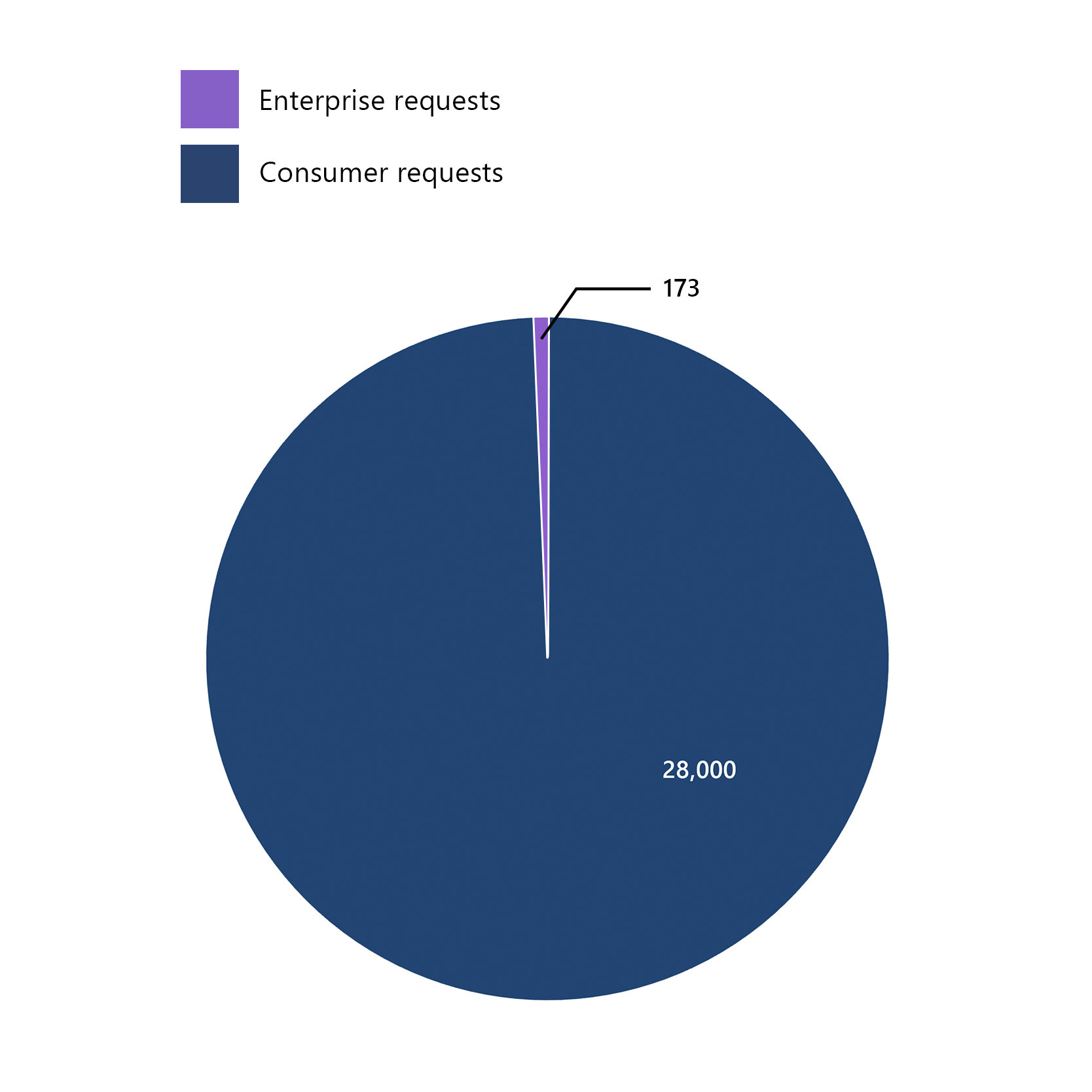
While Microsoft receives tens of thousands of law enforcement demands each year, well under 1% of those legal demands seek enterprise customer data. When Microsoft receives a demand for enterprise data, we always seek to redirect the requesting authority to seek the data from the enterprise itself, just like the authority would have done prior to the enterprise utilizing cloud services. We also provide notification to the enterprise unless prohibited by law.
View the Microsoft Enterprise One-Pager for July-December 2024
Total global law enforcement requests
Global enterprise requests
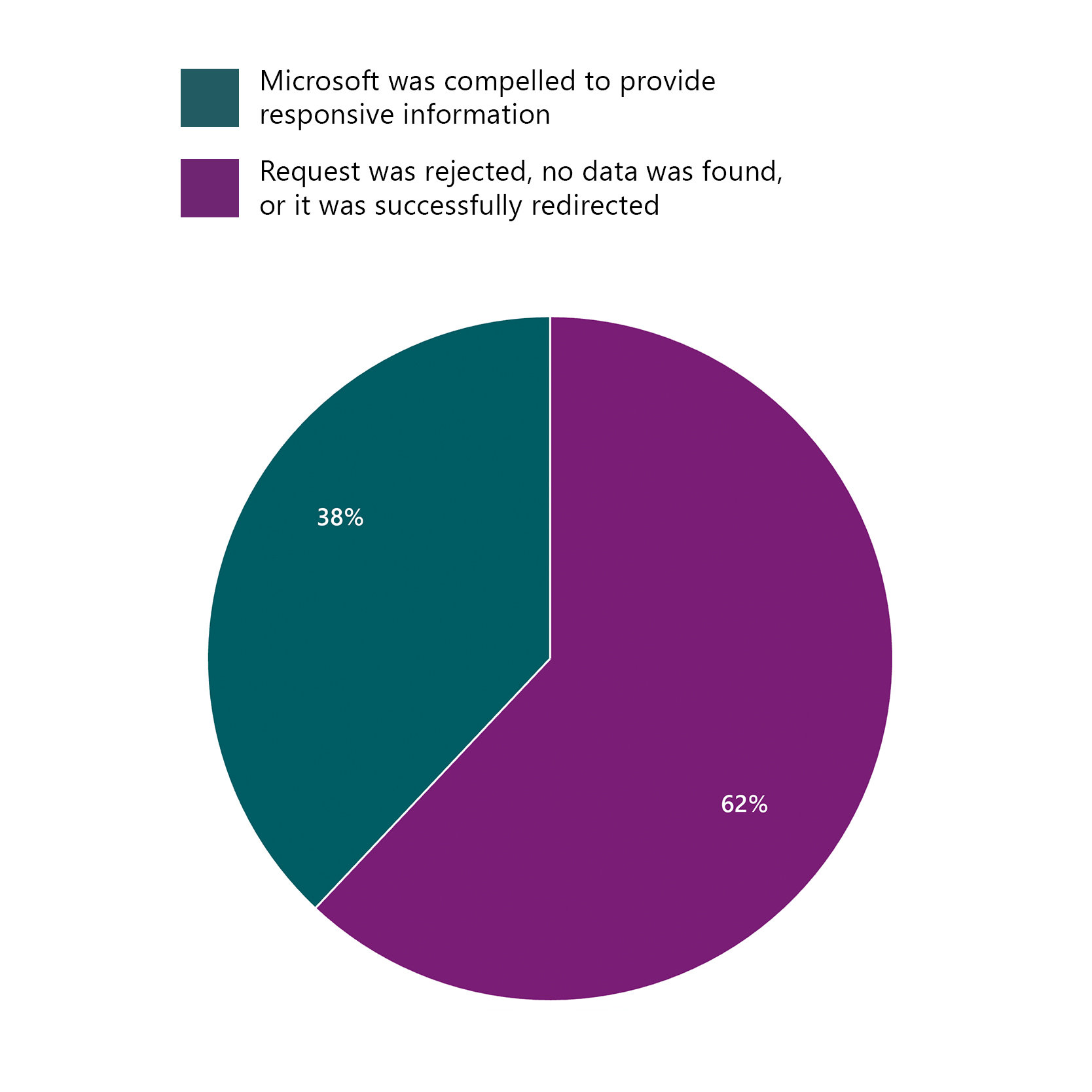
In the second half of 2024, Microsoft received 173 total requests from law enforcement around the world for accounts associated with enterprise cloud customers. Of those 173 requests:
- In 107 cases (62%), the requests were rejected, withdrawn, no data was available, or law enforcement was successfully redirected to the customer.
- In 66 cases (38%), Microsoft was compelled to provide responsive information:
- In 26 cases, we were required to disclose customer content.
- Twenty of such disclosures were associated with U.S. law enforcement.
- In 40 cases, we were required to disclose non-content data (e.g., such as basic subscriber information and IP logs).
- In 26 cases, we were required to disclose customer content.
- No disclosure involved Azure content data belonging to a commercial, public sector, or educational customer.
- No disclosure involved Dynamics 365 data.
Cross-Border Enterprise Disclosures:
- Of these 173 requests:
- Microsoft provided content data to U.S. law enforcement related to five non-U.S. enterprise customer whose data was stored outside the U.S. The customers were not based in the EU/EFTA.
FAQ regarding enterprise requests
-
Yes. When a request seeks data from one of our enterprise customers, we always attempt to redirect law enforcement authorities to obtain the information directly from our customer. Except in the most limited circumstances, we believe that law enforcement can go directly to commercial, educational, or government customers for information about one of their employees or accounts — just as law enforcement did before these customers moved to the cloud — and that they can do so without undermining their investigation. If appropriate, we may also file a formal legal challenge in court seeking to modify or quash a legal order.
-
Yes. Microsoft gives prior notice to its enterprise customers of any third-party requests for their data, except where prohibited by law. We also provide our enterprise customers with notice upon expiration of a valid and applicable nondisclosure order. We believe that our enterprise customers can, except in the most exceptional circumstances, be notified about government requests for their data. Even if a legal request is subject to a secrecy obligation, Microsoft will attempt to negotiate notice with the requesting governmental entity if we believe an appropriate contact with the enterprise could receive notification without jeopardizing the investigation, and we will file a formal legal challenge in court seeking to modify or withdraw a secrecy order if it is not supported by the law.
For additional information about how Microsoft responds to law enforcement requests for data, see the “General FAQ” section below.
U.S. National Security Orders Report
Prior to 2014, U.S. technology providers were not allowed to report any information regarding U.S. national security demands. As a result of litigation that Microsoft and other technology companies filed against the U.S. government in 2014, the government agreed for the first time to permit technology companies to publish data about FISA orders. This reporting structure was then codified as part of the USA FREEDOM Act. While there remain constraints on what we can publish, this report presents the most comprehensive, legally permissible picture of the types of requests that we receive from the U.S. government pursuant to its national security authorities.
We report on the number of orders received; however, receipt of an order does not mean Microsoft disclosed any information. We have successfully challenged requests in court, and will continue to do so, when we believe there are reasonable grounds for a challenge. Microsoft applies the same principles to any government demand for data regardless of whether that demand pertains to a criminal or national security investigation.
Foreign Intelligence Surveillance Act Orders
The data below reflects the most detailed information we may report pursuant to U.S. law on the aggregate number of orders received pursuant to FISA, and the range of accounts impacted during the most recent six-month period that the law allows us to report. This aggregate FISA data covers six-month periods but may only be published six months after the end of a reporting period.
| Reporting Period | Orders seeking disclosure of content | Accounts impacted by orders seeking content | Orders seeking disclosure of only non-content | Accounts impacted by non-content orders |
|---|---|---|---|---|
| Jul - Dec 2024 |
0 - 499
|
26,000 - 26,499
|
0 - 499
|
0 - 499
|
National Security Letters
The data below reflects the most detailed information Microsoft is permitted to report on the number of NSLs it has received in the most recent six-month period we are allowed to report.
| Reporting Period | Orders seeking disclosure of content | Accounts impacted by orders seeking content | Orders seeking disclosure of only non-content | Accounts impacted by non-content orders |
|---|---|---|---|---|
| Jul - Dec 2024 |
N/A
|
N/A
|
0 - 499
|
0 - 499
|
FAQ regarding U.S. national security orders
-
No. Microsoft adheres to the same principles for all types of government demands for user data and does so across all Microsoft services.
-
The Foreign Intelligence Surveillance Act of 1978, or FISA, is a U.S. law that authorizes certain types of foreign intelligence collection for national security purposes. A special independent federal court called the Foreign Intelligence Surveillance Court, or FISC, oversees such intelligence collection to ensure it is conducted consistent with the FISA statute and U.S. Constitution, including the Fourth Amendment protection against unreasonable searches and seizures.
-
FISA includes authorities to compel telecommunications and technology providers subject to U.S. jurisdiction to disclose certain communications and other content data as well as non-content data. The law also establishes important limitations on, and oversight of, those authorities.
Under FISA Section 702 (50 U.S. Code § 1881a et seq), the FISC may authorize the government to issue directives requiring companies to disclose content data, as well as non-content data, pertaining to specific non-U.S. persons located outside the U.S. in order to obtain certain judicially approved types of foreign intelligence information. This includes information to aid investigations into terrorism, weapons proliferation, and cybersecurity attacks. Based on a Presidential directive, Section 702 cannot be used to collect information for industrial espionage or to obtain a commercial advantage for U.S. businesses. Nor can Section 702 be used to suppress or burden criticism or dissent, or disadvantage persons based on their ethnicity, race, gender, sexual orientation, or religion. In addition to approving an annual certification of the Section 702 surveillance program, the FISC reviews all compliance incidents to ensure that any access is conducted in accordance with approved targeting procedures, the FISA statute, as well as the Constitution. The Department of Justice is also required to report any compliance incidents to Congress.
Other provisions of FISA authorize the government, under the supervision of the FISC, to compel the production of certain non-content data. This includes pen register and trap and trace orders under 50 U.S.C. § 1842 as well as, under limited circumstances, business record orders under FISA Section 215.
-
The number of user accounts impacted by Foreign Intelligence Surveillance Act (FISA) orders that were received or active during the period of time. Since individuals may have multiple accounts across different Microsoft services — all of which are counted separately to determine the number of accounts impacted — this number will likely overstate the number of individuals subject to government orders.
-
National Security Letters may require the disclosure of basic subscriber information such as the name, address and length of service of a customer who has subscribed to one of our services. NSLs, codified under 18 U.S. Code § 2709, may not be used to require the disclosure of the content of a customer’s communications or data. NSLs may only be used to request basic subscriber information that is relevant to U.S. national security and cannot be used for criminal, civil, or administrative investigations.
The U.S. government is required to report to Congress twice a year on how it uses NSLs and the Department of Justice audits the FBI’s use of NSLs to ensure compliance with the law.
-
No. All such orders that were received or active during the reporting period are reflected in this report.
-
Executive Order (EO) 12333 is a Presidential directive that organizes U.S. intelligence activities and regulates the foreign intelligence collection of certain components of the U.S. Intelligence Community. Importantly, EO 12333 does not include any authorization to compel private companies, such as Microsoft, to disclose customer data, and Microsoft would not comply with a request from the U.S. government under EO 12333 for Microsoft to voluntarily provide personal data.
-
Microsoft applies the same principles to any government demand for data and will notify customers except when prohibited by law. Microsoft also provides notice to customers upon expiration of a valid and binding nondisclosure order.
Pursuant to 18 U.S.C. § 2709(c)(1), the FBI may prohibit Microsoft from disclosing the receipt of an NSL if it certifies that disclosure may result in “a danger to the national security of the United States, interference with a criminal, counterterrorism, or counterintelligence investigation, interference with diplomatic relations, or danger to the life or physical safety of any person.” As a result of reforms in the USA FREEDOM Act, the FBI periodically reviews the need for non-disclosure provisions associated with previously issued NSLs. When we receive notice from the FBI that an NSL is no longer subject to a non-disclosure obligation and we are no longer prohibited from providing notice, we notify our customers.
Current law prohibits recipients of FISA orders from ever disclosing the existence of a FISA order.
-
U.S. law prohibits us from disclosing more specific information regarding national security legal demands including FISA orders and NSLs. Microsoft disagrees with these laws and believes that greater transparency is critical to maintaining trust in the rule of law. Both in courts and in Congress, Microsoft has a long and successful history of advocating for additional transparency, and we are committed to working with policy makers to continue expanding our ability to provide more meaningful information to the public.
-
Microsoft applies the same principles to any government demand for data. We believe that governments should never place global technology providers in the middle of state-on-state intelligence gathering. Microsoft would challenge any demand for foreign public sector data from any government.
-
Countries around the world have legal authorities that allow governments to compel certain information from private companies in support of national security investigations. If Microsoft receives such a demand, we apply the same principles we do to any other government demand for data. These requests would be included in this Government Requests Report.
Data Access Agreement Requests
The CLOUD Act authorized the U.S. government to enter into data access agreements with other governments to resolve potential conflicts of law and establish clear, privacy-protective rules to govern cross-border requests for digital evidence when investigating serious crime.
As of the date of this report, the U.S. government has entered into agreements with the United Kingdom and Australia, and has announced negotiations with Canada and the European Union.
Importantly, these agreements do not provide any new surveillance authorities to any government. The agreements merely remove U.S. legal restrictions that had previously forced the foreign law enforcement authorities to send evidence requests through the Mutual Legal Assistance (MLA) process. The lengthy, bureaucratic MLA process requires requests to be individually approved by the U.S. Department of Justice and a U.S. court before being forwarded to U.S-based technology companies. This did not prevent the foreign law enforcement authorities from obtaining data from U.S. technology providers, it merely slowed them down – often at the cost of public safety. The data access agreements allow certain foreign law enforcement requests pertaining to serious crime and terrorism, consistent with rule of law and human rights requirements, to be routed directly to U.S. technology companies.
Requests are reported in accordance with applicable restrictions from laws of the listed country.
Requests received under Data Access Agreements in the second half of 2024
| Location | Reporting Period | Orders seeking disclosure of content | Accounts impacted by orders seeking content | Orders seeking disclosure of only non-content | Accounts impacted by non-content orders |
|---|---|---|---|---|---|
| United Kingdom |
Jul - Dec 2024
|
500 - 999
|
500 - 999
|
0 - 499
|
0 - 499
|
| Australia |
Jul - Dec 2024
|
0 - 499
|
0 - 499
|
0 - 499
|
0 - 499
|
FAQ regarding data access agreement requests
-
We included requests invoking data access agreements separately both because they may be subject to reporting restrictions different from other law enforcement requests and because it provides us with an opportunity to explain the benefits of these agreements as well as address misperceptions.
-
Yes. Technology providers are still able to challenge any government demand that may be unlawful or otherwise inconsistent with the agreement. Further, the principle of comity, which allows a challenge based on an international conflict of law, is well-established in countries with data access agreements. And the CLOUD Act codified the ability of providers to challenge an order under U.S. law based on comity. The agreements also have no enforcement mechanism and impose no enforcement obligations on either party. They merely remove the above-mentioned U.S. legal prohibitions in certain circumstances.
-
No. An agreement only recognizes and eliminates conflicting legal obligations so that technology companies can respond to legal orders received in connection with the investigation of a serious criminal offense over which the requesting country already has jurisdiction under its existing domestic laws. The agreement does not expand the scope of either country’s laws or their jurisdiction.
-
No. The CLOUD Act does not allow the foreign government to use the agreement to target individuals or entities residing in the U.S. And agreements to date have recognized the inverse: The U.S. government is not permitted to seek from foreign providers data pertaining to individuals or entities residing in the foreign country. So, for example, the U.S. would not be permitted to seek data pertaining to an UK person or enterprise from an UK provider under the agreement, nor would UK law enforcement be permitted to seek U.S. person or enterprise data from a U.S. provider. The MLAT process remains for such requests.
-
The CLOUD Act is encryption neutral and does not require providers to comply with data access demands or technical assistance laws.
-
Microsoft receives various forms of legal requests seeking information or actions from UK authorities. Those can include preservation requests as well as demands for content and non-content data. Warrants for content and non-content are governed by the UK’s Crime (Overseas Production Orders) Act 2019 (COPO), and the Investigatory Powers Act (IPA) and accompanying regulations for offenses under criminal and national security investigations. Additionally, the UK can seek emergency disclosures of data in situations where there is imminent harm to life or safety.
-
For requests under the Investigatory Powers Act, and as reflected in this report, Microsoft is required by UK law to report only the number of total requests and specified accounts on a 6-month delay and in ranges of 500. This limitation is found in The Investigatory Powers (Disclosure of Statistical Information) Regulations 2018.
-
Yes, Microsoft adheres to the same principles and commitments related to U.S. government demands for user data. Neither the CLOUD Act nor the data access agreements in effect changed any of the legal and privacy protections that previously applied to law enforcement requests for data – and those protections continue to apply. Further, requests are carefully reviewed for legal sufficiency.
Civil Requests
Microsoft receives legal demands for customer data from civil litigation parties around the world. Microsoft does not respond to private requests other than those received through a valid legal process. Microsoft adheres to the same principles for all civil proceeding legal requests as it does for government agency requests for user data, requiring nongovernmental civil litigants to follow the applicable laws, rules, and procedures for requesting customer data.
If a nongovernmental party seeks customer data, it needs to follow applicable legal process — meaning, it must serve us with a valid subpoena or court order for content or subscriber information or other non-content data. For content requests, we require specific lawful consent of the account owner and for all requests we provide notice to the account owner unless prohibited by law from doing so. We require that any requests be targeted at specific accounts and identifiers. The Microsoft compliance team reviews civil proceeding legal requests for user data to ensure the requests are valid and only provides the data specified in the legal order. A summary of the Microsoft team’s responses to civil litigation requests for customer data is included in the downloadable version of this report.
Except where prohibited by law, Microsoft will give prior notice to customers whose data is sought by a civil proceeding litigant. Microsoft sometimes receives civil proceeding legal demands that prohibit us from notifying our customer. In some cases, we request permission to notify our customer or even challenge the nondisclosure order. In some cases, Microsoft has persuaded the requesting party that its interests in the underlying litigation will not be prejudiced by Microsoft providing notice.
Government Requests Reports
-
Law Enforcement Requests Report 2024 (July-December)
Law Enforcement Requests Report 2024 (January-June)
Law Enforcement Requests Report 2023 (July-December)
Law Enforcement Requests Report 2023 (January-June)
Law Enforcement Requests Report 2022 (July-December)
Law Enforcement Requests Report 2022 (January-June)
Law Enforcement Requests Report 2021 (July-December)
Law Enforcement Requests Report 2021 (January-June)
Law Enforcement Requests Report 2020 (July-December)
Law Enforcement Requests Report 2020 (January-June)
Law Enforcement Requests Report 2019 (July-December)
Law Enforcement Requests Report 2019 (January-June)
Law Enforcement Requests Report 2018 (July-December)
Law Enforcement Requests Report 2018 (January-June)
Law Enforcement Requests Report 2017 (July-December)
Law Enforcement Requests Report 2017 (January-June)
Law Enforcement Requests Report 2016 (July-December)
Law Enforcement Requests Report 2016 (January-June)
Law Enforcement Requests Report 2015 (July-December)
Law Enforcement Requests Report 2015 (January-June)
Law Enforcement Requests Report 2014 (July-December)
Law Enforcement Requests Report 2014 (January-June)
Law Enforcement Requests Report 2013 (July-December)
General FAQ
Questions about Microsoft’s law enforcement requests principles
-
Governments play a critical role in keeping the public safe. They had the legal means to investigate and access people’s personal information before modern cloud technology existed. They continue to have those legal means today. Microsoft has a team that works around the clock to respond rapidly when governments’ demands for data are legal, valid, and compulsory. At the same time, we believe our customers deserve predictability in how and when a government can access their data. We place a premium on respecting and protecting the privacy of our customers, and work to earn their trust every day. Our customers own both their “content data” and “non-content data,” and we regularly challenge government requests for data where there is a lawful basis for doing so. By only responding to valid legal process, we strive to offer customers clear expectations for what happens with their data.
-
As our law enforcement requests reports over the years have shown, the overwhelming majority of requests seek information related to our free consumer services. By comparison, we have received very few requests for data associated with our commercial services used by enterprise customers. More information on both consumer and enterprise requests is included in this report.
-
As our reports show, every year we reject a number of law enforcement requests. Challenges to government requests can take many forms. In many of these cases, we simply inform the requesting government that we are unable to disclose the requested information and explain our reason for rejecting the request. We also, where it is appropriate, challenge requests in court.
There are many reasons why Microsoft may reject or challenge a request. For example, we might reject a request if it is facially invalid, improperly served on us, or requests data of a type not supported by the order or of the incorrect technology company. We may reject requests when they exceed the authority or jurisdiction of the requesting agency. We may reject a request if it is not signed or not appropriately authorized, contains the wrong dates, is not properly addressed, contains material mistakes, or is overly broad.
-
Our Global Human Rights Statement outlines our commitment to respect the universal human rights of our customers. By verifying law enforcement entities followed the laws and procedures in their jurisdictions before we respond to a request, we seek to ensure we are disclosing customer data only in authorized criminal investigations. Even when compliant with the laws of the requesting agency’s jurisdiction, Microsoft challenges law enforcement requests for enterprise customer data when the privacy regulations of the jurisdiction where the data host is located conflict with the laws of the requesting jurisdiction.
-
Microsoft produces data in response to valid legal requests from governmental entities in countries where Microsoft Corporation is located. We conduct a local legal review of each request we receive against both the local laws and standards and our own standards. We also periodically review our screening processes around the world to ensure we are following local judicial procedures and applying our Global Human Rights Statement.
-
Non-content data includes basic subscriber information, such as an email address, name, state, country, ZIP code, and IP address at time of registration. Other non-content data may include IP connection history, an Xbox Gamertag, and credit card or other billing information. We require a valid legal demand, such as a subpoena or court order, before we will consider disclosing non-content data to law enforcement.
Content is what our customers create, communicate, and store on or through our services, such as the words in an email exchanged between friends or business colleagues or the photographs and documents stored on OneDrive or other cloud offerings. We require a warrant or its equivalent before we will consider disclosing content to law enforcement.
-
No. We believe that you should control your own data. Microsoft does not give any government (including law enforcement, or other government entities) direct or unfettered access to customer data.
-
No. Microsoft does not build back doors into any of its products. We’ve been clear that we do not provide direct, unfettered access to customer data, and history shows we have a track record of declining requests to give voluntary access to customer data.
-
The U.S. law, Communications Assistance for Law Enforcement Act, does not currently apply to many Microsoft services, including Skype, because they are not considered telecommunications services.
-
Many of our products use end-to-end encryption or deploy encryption extensively. We invest in encryption because it protects our customers from a range of threats including cybercrime. However, sometimes our customers wish to deploy technologies to fight cybercrime or provide another feature that require content to be decrypted in a secure environment somewhere in the process. For example, some customers may wish to run enterprise software that scans emails to detect phishing attacks or malicious code. Customers may also wish to take advantage of features like real-time language translation in Skype calls, which require us to temporarily and securely decrypt data. Our approach is to give customers choices while continuously working to improve encryption and other security measures so they can be applied broadly. Details on the encryption deployed in our products are regularly updated and can often be viewed by visiting the website associated with that product.
-
We do not provide any government with Microsoft’s encryption keys or the ability to break our encryption. In most cases, our default is for Microsoft to securely store customers’ encryption keys. Even Microsoft’s largest enterprise customers usually prefer that we keep their keys to prevent accidental loss or theft. However, in many circumstances we also offer the option for consumers or enterprises to keep their own keys, in which case Microsoft does not maintain copies.
-
Yes. All government requests for data, including any that were accompanied by non-disclosure orders, also known as secrecy orders, are included in our transparency reports. Microsoft has a long history of successfully challenging unnecessary secrecy orders, both directly in communications with law enforcement and formally in court. Microsoft has also advocated in Congress to reform the U.S. non-disclosure order statute, 18 U.S.C. § 2705, to ensure that such orders are properly narrowed, time-limited, and only approved by judges when truly necessary to protect a criminal investigation.
-
Services in the European Union are provided by Microsoft Ireland Operations Limited (MIOL), which is incorporated in Ireland. All of our European datacenters are owned or leased by MIOL and its subsidiaries. Information about Microsoft datacenter locations is available at Azure global infrastructure. Information about services available within the European Union Data Boundary (EUDB) is available in the Product Terms, and information about M365 Advanced Data Residency (ADR) is available at Overview of Advanced Data Residency.
Questions about Microsoft’s law enforcement requests practices
-
Microsoft requires official, signed, legally valid process issued pursuant to federal or local law and rules. Specifically, we require a subpoena or its equivalent before disclosing non-content, and only disclose content to law enforcement in response to a warrant (or its local equivalent). Microsoft’s global compliance teams review government demands for customer data to ensure the requests are valid, reject those that are not valid, and only provide the data specified in the legal order. Moreover, Microsoft redirects the government to seek data from enterprise customers themselves when legally permitted. All law enforcement requests arrive at Microsoft through a secure portal for use by vetted law enforcement agencies and personnel. Once Microsoft reviews the demand and determines that it must provide data, the data specified in the valid legal order is provided to law enforcement through the same, secure portal.
-
We do this only in limited, defined circumstances. Pursuant to U.S. law, we are required to report identified or suspected images exploiting children to the U.S. National Center for Missing and Exploited Children (NCMEC). On occasion, we also report some limited information about a user when we have reason to believe the individual is about to harm themselves or someone else due to a public posting on one of our forums, on Xbox LIVE, or through referrals from other customers. If one of our customers or employees, or Microsoft itself, is the victim of a crime, we may report some limited information to law enforcement. Additionally, consistent with applicable law and industry practice, Microsoft sometimes discloses limited information to law enforcement where we believe the disclosure is necessary to prevent an emergency involving danger of death or serious physical injury to a person.
-
Yes. Microsoft considers emergency requests from law enforcement agencies around the world when a disclosure is necessary to prevent an emergency involving danger of death or serious physical injury to a person. Microsoft requires these requests be in writing on official letterhead, and signed by a law enforcement authority. The request must contain a description of the emergency, along with an explanation of how the information sought will assist law enforcement in addressing the emergency. Each request is carefully evaluated by Microsoft’s compliance team before any data is disclosed, and the disclosure is limited to the data that we believe would enable law enforcement to address the emergency. Some of the most common emergency requests involve suicide threats, kidnappings, and other threats of imminent violence. Every six months, we publish information about the emergency requests we receive in this report.
-
Yes. We require a warrant (or equivalent process) before we will consider releasing content. Like other companies, we’ve implemented the holding of U.S. v. Warshak, which says that email users maintain a reasonable expectation of privacy in the content of their emails. In order to obtain a warrant for data, the government must present the evidence it possesses to a judge and convince that judge that probable cause exists to believe a crime has been committed, and evidence of that crime will be found in the data it seeks. Moreover, the alleged crime must have some connection with the jurisdiction seeking the warrant. Because the government can obtain a subpoena with much less rigor, the law prohibits the disclosure of content data via subpoena. Microsoft would similarly reject any other court order for content that falls below the warrant, or equivalent, standard based on probable cause.
-
No. Sometimes we seek to narrow the scope of requests, either by seeking to limit the type or amount of data to be provided or by requesting the government seek the data directly from the customer. If appropriate, we may also file a formal legal challenge in court seeking to modify or quash a legal order.
-
Microsoft has long believed that secrecy should be the exception, used only temporarily and when clearly necessary to protect sensitive investigations, rather than the norm. Microsoft has repeatedly and successfully challenged the U.S. government to limit its use of non-disclosure or secrecy orders, which prevent us from notifying our customers of a government demand for their data. See Ensuring secrecy orders are the exception not the rule when the government seeks data owned by our customers - Microsoft On the Issues and Continued progress and support in fighting secrecy orders - Microsoft On the Issues. In 2021, Microsoft provided testimony to the U.S. House of Representatives Committee on the Judiciary in support of statutory reforms to the secrecy order statute. See The need for legislative reform on secrecy orders - Microsoft On the Issues.
In the second half of 2024, Microsoft received secrecy orders attached to 35% percent of U.S. legal demands, including federal, state, and local law enforcement demands, totaling 3864 secrecy orders. Of these, 3190 were issued by federal law enforcement authorities.
-
Sometimes. Pursuant to U.S. law, Microsoft is entitled to seek reimbursement for costs associated with compliance with a valid legal demand. We only charge in an attempt to recover some costs associated with the need to comply with U.S. legal demands. To be clear, these reimbursements cover only a portion of the costs that we actually incur to comply with legal orders. We do not, however, charge in emergency situations or in known child exploitation investigations. For additional information about how we use and protect customer information, please read the Microsoft Privacy Statement.

